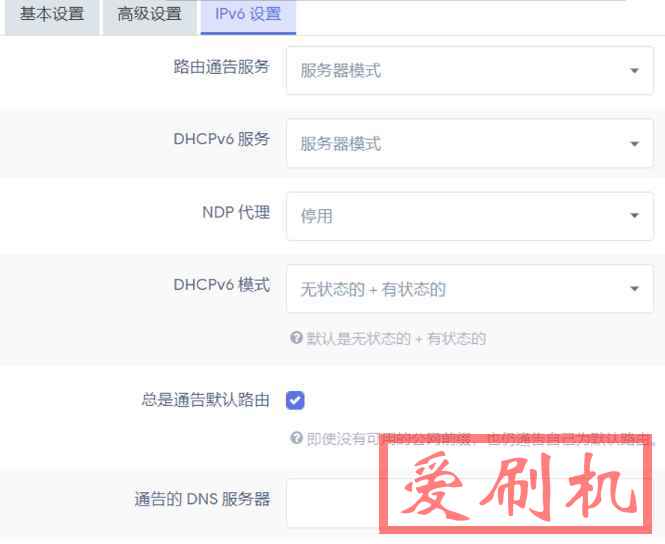
padavan老毛子被SSH远程爆破登录路由器设置远程登录黑白名单
今天查询日志发现大量这样的信息,搜索一下,应该是正在被远程暴力破解。
由于家里宽带是公网IP,又开启了SSH,导致路由器被爆破登录。
IP似乎是固定的这个,如何能屏蔽这个IP呢?有经验的坛友请指教一下呗。
Aug 19 10:59:50 dropbear[22589]: Exit before auth: Exited normally
Aug 19 11:10:20 dropbear[23565]: Child connection from 141.98.81.42:44711
Aug 19 11:10:23 dropbear[23565]: Bad password attempt for 'admin' from 141.98.81.42:44711
Aug 19 11:10:24 dropbear[23565]: Exit before auth (user 'admin', 1 fails): Exited normally
Aug 19 11:10:25 dropbear[23581]: Child connection from 141.98.81.207:42523
Aug 19 11:10:27 dropbear[23581]: Bad password attempt for 'admin' from 141.98.81.207:42523
Aug 19 11:10:28 dropbear[23581]: Exit before auth (user 'admin', 1 fails): Exited normally
Aug 19 11:10:29 dropbear[23582]: Child connection from 141.98.81.208:37185
Aug 19 11:10:32 dropbear[23582]: Login attempt for nonexistent user from 141.98.81.208:37185
Aug 19 11:10:33 dropbear[23582]: Exit before auth: Exited normally
Aug 19 11:10:33 dropbear[23598]: Child connection from 141.98.81.209:43151
Aug 19 11:10:36 dropbear[23598]: Bad password attempt for 'admin' from 141.98.81.209:43151
Aug 19 11:10:36 dropbear[23598]: Exit before auth (user 'admin', 1 fails): Exited normally
Aug 19 11:10:37 dropbear[23599]: Child connection from 141.98.81.210:38917
Aug 19 11:10:40 dropbear[23599]: Login attempt for nonexistent user from 141.98.81.210:38917
Aug 19 11:10:41 dropbear[23599]: Exit before auth: Exited normally
Aug 19 11:10:41 dropbear[23615]: Child connection from 141.98.81.15:39858
Aug 19 11:10:44 dropbear[23615]: Login attempt for nonexistent user from 141.98.81.15:39858
Aug 19 11:10:45 dropbear[23615]: Exit before auth: Exited normally
Aug 19 11:10:45 dropbear[23616]: Child connection from 141.98.81.42:40047
Aug 19 11:10:48 dropbear[23616]: Login attempt for nonexistent user from 141.98.81.42:40047
Aug 19 11:10:49 dropbear[23616]: Exit before auth: Exited normally
Aug 19 11:10:49 dropbear[23617]: Child connection from 141.98.81.207:44823
Aug 19 11:10:52 dropbear[23617]: Login attempt for nonexistent user from 141.98.81.207:44823
Aug 19 11:10:53 dropbear[23617]: Exit before auth: Exited normally
Aug 19 11:10:53 dropbear[23633]: Child connection from 141.98.81.208:39915
Aug 19 11:10:56 dropbear[23633]: Login attempt for nonexistent user from 141.98.81.208:39915
Aug 19 11:10:57 dropbear[23633]: Exit before auth: Exited normally
Aug 19 11:10:57 dropbear[23634]: Child connection from 141.98.81.209:44223
Aug 19 11:11:00 dropbear[23634]: Login attempt for nonexistent user from 141.98.81.209:44223
Aug 19 11:11:01 dropbear[23634]: Exit before auth: Exited normally
Aug 19 11:11:01 dropbear[23650]: Child connection from 141.98.81.210:40893
Aug 19 11:11:04 dropbear[23650]: Login attempt for nonexistent user from 141.98.81.210:40893
Aug 19 11:11:05 dropbear[23650]: Exit before auth: Exited normally
Aug 19 11:11:05 dropbear[23651]: Child connection from 141.98.81.15:44770
Aug 19 11:11:08 dropbear[23651]: Login attempt for nonexistent user from 141.98.81.15:44770
Aug 19 11:11:09 dropbear[23651]: Exit before auth: Exited normally
Aug 19 11:11:10 dropbear[23652]: Child connection from 141.98.81.42:35837
Aug 19 11:11:13 dropbear[23652]: Login attempt for nonexistent user from 141.98.81.42:35837
Aug 19 11:11:14 dropbear[23652]: Exit before auth: Exited normally
Aug 19 11:11:14 dropbear[23668]: Child connection from 141.98.81.207:39787
Aug 19 11:11:17 dropbear[23668]: Bad password attempt for 'admin' from 141.98.81.207:39787
Aug 19 11:11:18 dropbear[23668]: Exit before auth (user 'admin', 1 fails): Exited normally
Aug 19 11:11:18 dropbear[23669]: Child connection from 141.98.81.208:45883
Aug 19 11:11:21 dropbear[23669]: Login attempt for nonexistent user from 141.98.81.208:45883
Aug 19 11:11:22 dropbear[23669]: Exit before auth: Exited normally
Aug 19 11:11:22 dropbear[23685]: Child connection from 141.98.81.209:35055
Aug 19 11:11:25 dropbear[23685]: Login attempt for nonexistent user from 141.98.81.209:35055
Aug 19 11:11:26 dropbear[23685]: Exit before auth: Exited normally
Aug 19 11:11:26 dropbear[23686]: Child connection from 141.98.81.210:38325
Aug 19 11:11:29 dropbear[23686]: Bad password attempt for 'admin' from 141.98.81.210:38325
Aug 19 11:11:30 dropbear[23686]: Exit before auth (user 'admin', 1 fails): Exited normally
Aug 19 11:11:30 dropbear[23687]: Child connection from 141.98.81.15:50004
Aug 19 11:11:33 dropbear[23687]: Login attempt for nonexistent user from 141.98.81.15:50004
Aug 19 11:11:34 dropbear[23687]: Exit before auth: Exited normally
Aug 19 11:13:32 dropbear[23883]: Child connection from 85.209.0.252:48846
Aug 19 11:13:32 dropbear[23883]: Exit before auth: Exited normally
Aug 19 11:13:33 dropbear[23884]: Child connection from 85.209.0.252:41624
Aug 19 11:13:33 dropbear[23885]: Child connection from 85.209.0.252:41626
Aug 19 11:13:34 dropbear[23885]: Login attempt for nonexistent user from 85.209.0.252:41626
Aug 19 11:13:36 dropbear[23885]: Exit before auth: Exited normally
Aug 19 11:13:36 dropbear[23884]: Login attempt for nonexistent user from 85.209.0.252:41624
Aug 19 11:13:39 dropbear[23884]: Exit before auth: Exited normally
Aug 19 11:17:09 dropbear[24201]: Child connection from 87.251.74.30:42172
Aug 19 11:17:10 dropbear[24201]: Exit before auth: Exited normally
Aug 19 11:17:10 dropbear[24202]: Child connection from 87.251.74.30:33526
Aug 19 11:17:10 dropbear[24203]: Child connection from 87.251.74.30:33338
Aug 19 11:17:12 dropbear[24202]: Login attempt for nonexistent user from 87.251.74.30:33526
Aug 19 11:17:12 dropbear[24203]: Login attempt for nonexistent user from 87.251.74.30:33338
Aug 19 11:17:13 dropbear[24219]: Child connection from 87.251.74.30:52856
Aug 19 11:17:13 dropbear[24202]: Exit before auth: Exited normally
Aug 19 11:17:13 dropbear[24203]: Exit before auth: Exited normally
Aug 19 11:17:14 dropbear[24219]: Login attempt for nonexistent user from 87.251.74.30:52856
Aug 19 11:17:15 dropbear[24219]: Exit before auth: Exited normally
Aug 19 11:29:36 dropbear[25330]: Child connection from 87.251.74.6:19524
Aug 19 11:29:36 dropbear[25330]: Exit before auth: Exited normally
Aug 19 11:29:36 dropbear[25331]: Child connection from 87.251.74.6:34934
Aug 19 11:29:36 dropbear[25332]: Child connection from 87.251.74.6:40472
Aug 19 11:29:38 dropbear[25332]: Login attempt for nonexistent user from 87.251.74.6:40472
Aug 19 11:29:38 dropbear[25331]: Login attempt for nonexistent user from 87.251.74.6:34934
Aug 19 11:29:40 dropbear[25331]: Exit before auth: Exited normally
Aug 19 11:29:40 dropbear[25332]: Exit before auth: Exited normally
Aug 19 11:29:41 dropbear[25333]: Child connection from 87.251.74.6:26390
Aug 19 11:29:42 dropbear[25333]: Login attempt for nonexistent user from 87.251.74.6:26390
Aug 19 11:29:43 dropbear[25333]: Exit before auth: Exited normally
Aug 19 11:44:30 dropbear[26717]: Child connection from 194.180.224.130:43924
Aug 19 11:44:30 dropbear[26718]: Child connection from 194.180.224.130:43922
Aug 19 11:44:30 dropbear[26719]: Child connection from 194.180.224.130:43928
Aug 19 11:44:36 dropbear[26717]: Login attempt for nonexistent user from 194.180.224.130:43924
Aug 19 11:44:36 dropbear[26718]: Login attempt for nonexistent user from 194.180.224.130:43922
Aug 19 11:44:38 dropbear[26719]: Bad password attempt for 'admin' from 194.180.224.130:43928
Aug 19 11:44:41 dropbear[26719]: Exit before auth (user 'admin', 1 fails): Exited normally
Aug 19 11:44:41 dropbear[26717]: Exit before auth: Exited normally
Aug 19 11:44:41 dropbear[26718]: Exit before auth: Exited normally
Aug 19 11:46:17 dropbear[26886]: Child connection from 65.49.20.66:31298
Aug 19 11:46:18 dropbear[26886]: Login attempt for nonexistent user from 65.49.20.66:31298
Aug 19 11:46:22 dropbear[26886]: Exit before auth: Exited normally
Aug 19 11:48:40 dropbear[27097]: Child connection from 187.16.255.102:41142
Aug 19 11:48:40 dropbear[27097]: Exit before auth: Exited normally
Aug 19 12:07:12 dropbear[28779]: Child connection from 187.16.255.102:54228
Aug 19 12:07:12 dropbear[28779]: Exit before auth: Exited normally
现在先把SSH关闭了,等需要用了 再打开。
限制ip SSH远程登录
有时候为了服务器的安全考虑,我们可以在服务器上做限制,禁止其他ip地址连接服务器。
方法一:修改ssh配置文件
其实做这个操作很简单,只需要改/etc/ssh/sshd_config配置文件,再最后一行添加下面语句即可
allowusers root@49.4.151.24 ##注意此处添加的ip地址应为内网出口的公网ip地址,而不是局域网的内网 ipallowusers root@1.119.144.11 ##可以添加多行,表示容许多个ip访问服务器
修改完毕后重启ssh
/etc/init.d/sshd restart
测试
可以新建个用户,然后使用新用户登录,看能否登录上;还可以让朋友登录测试
如果测试过程中有问题,可以看登录日志
tail -f /var/log/secure
日志中就可以看出来,我设置的内网ip并没有出现在日志中,而是一个公网ip,由此可以看出,配置文件识别的是公网ip(此也可以看出来自己的公网ip地址),修改配置文件
中的内网ip为公网ip后,测试通过。
方法二:修改两个配置文件
/etc/hosts.allow和/etc/hosts.deny
/etc/hosts.allow和/etc/hosts.deny两个文件是控制远程访问设置的,通过他可以允许或者拒绝某个ip或者ip段的客户访问linux的某项服务。
比如SSH服务,我们通常只对管理员开放,那我们就可以禁用不必要的IP,而只开放管理员可能使用到的IP段;
首先编辑允许连接服务器的ip,即可以放行的ip
Vim /etc/hosts.allow
添加一行
sshd:49.4.151.24:allow #此处ip仍然为局域网出口的公网ip
如果有多台服务器,比如我们有多台云服务器,那么这个允许的ip地址可能不一样,可以在登录服务器上会有ip地址提示,如下
然后编辑禁止连接服务器的ip地址
vim /etc/hosts.deny
输入(表示除了上面允许的,其他的ip 都拒绝登陆ssh)
sshd:ALL
编辑完上面两个文件后,无需重启任何配置文件,即时生效
上面两种方法对比的区别在于第一种方法限制范围更强,不仅限制了ip,而且用户不对,也登录不了服务器;
第二种方法只限制了ip地址,只要密码正确,用户名不同也可以登录,这种适用于局域网中有多人需要登录服务器的需求。
注意:
/etc/hosts.deny中的设置会影响ansible远程管理,如果需要ansible管理,可以将ansible所在的服务器地址(如果使用的私网ip,那么添加私网ip)添加到/etc/hosts.allow中
sshd:10.172.288.60:allow
本站附件分享,如果附件失效,可以去找找看